Cyber Security.
We protect your business against ever-evolving threats to your IT security, both online and offline. Constantly under threat, your cyber security should be encountered in a proactive manner, even small changes can greatly improve your cyber defences. We offer a comprehensive portfolio of sophisticated, resilient IT security solutions, making sure you have a robust cyber security system, so your data stays protected, and you can focus on growing your business.
Our experienced and accredited IT security team based in Northampton can help you to protect your business against cyber criminals, reviewing the threat landscape and responding to new security risks. As an IASME Licensed Certification Body we offer auditing consultancy, as well as for the government-led Cyber Essentials certification.

Cyber Security For SMB’s
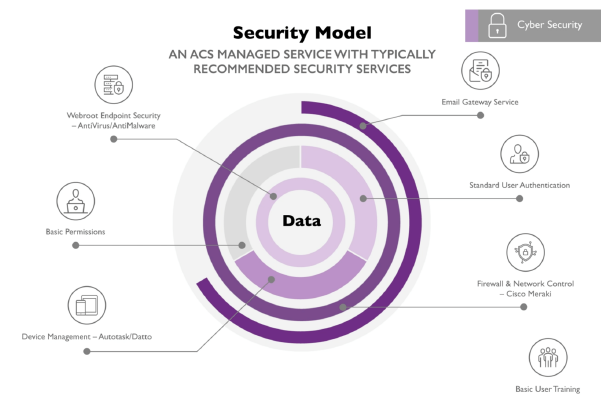
ACS Office Solutions uses the latest cutting-edge technology to protect companies and organisations. With one comprehensive cloud-native platform, we defend companies and organisations by using artificial intelligence and computer vision to monitor systems for suspicious activity.
Secure your Investment
We can’t all monitor our IT infrastructure 24/7 and react when a threat becomes reality. As cyber threats become more sophisticated and the stakes rise, a breach will, at minimum, cost time and money to rectify. At worst, a security incident could cause the complete failure of a business. Trust ACS to help protect your business.

HP Wolf Security – Advanced Security In-The-Box
Face the future with confidence, The world’s most secure and manageable PCs are designed to be resilient against the attacks of tomorrow. HP Elitebook 845 G8 Pro Security Edition, Designed for how you work – The HP EliteBook 845 is built for how you work today.
Resources
ACS Systems acquired by multinational technology company
ACS Systems has been acquired by multinational technology company, Bechtle. Founded in 1983, Bechtle is now one of Europe’s leading IT providers with a presence in 14 countries. In the past, Bechtle direct ...
Evolution of the MSP
Watch Sessions After almost three years, ACS returned to the University of Northampton for their ‘Evolution of the MSP’ event. Guest speakers included Steve Horobin of Arrow, Greg Bayliss of Cymulate and Stephen ...
Strengthening your first line of defence
As businesses fight the war against phishing attacks and cyber security breaches, staff are, in the words of one data systems manager, both the weakest link and the first line of defence. Doug Frost, ...