Resources.
Strengthening your first line of defence
As businesses fight the war against phishing attacks and cyber security breaches, staff are, in the words of one data systems manager, both the weakest link and the first line of defence. Doug Frost, ...
MHA MacIntyre Hudson Colchester
Refurbishing an office requires so much more forethought since the pandemic made workers think long and hard about what they want from an office, or whether they want to be in an office at all.
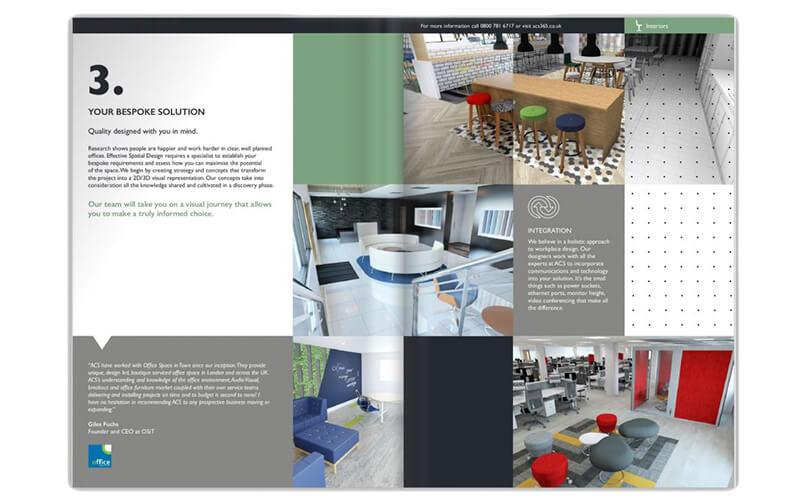
Success Based on Building Excellent Relationships
Solid project knowledge and an understanding of the market not only gave ACS the opportunity to deliver a furniture fit-out for the UK’s largest recruitment company.
Roll-out continues as school learns what works best
Rolling out devices to staff, faculty, and pupils at the third largest co-educational boarding school in the UK was always going to be a challenge.
Building a valuable relationship that keeps processes running smoothly
It doesn’t matter if you’ve been in business for a year or 100 years, the need to evolve and keep IT systems working efficiently remains the same
Helping Clients Negotiate Every Hurdle – Government Case Study
There are times when an honest appraisal of a situation, even if it’s not necessarily what the client wants to hear, is the only way to ensure trust and positive outcomes on both sides. ...
Building a Futureproof and Reliable Solution for Kilby Fox
Kilby Fox turned to ACS when it became apparent that their existing system could not provide the speed needed for a busy, modern office.
Tec, Fire And Security – Telecoms Placed In Safe Hands
With an office move providing an opportunity for further expansion, the directors at TEC Fire and Security knew that the firm’s telephone system would have to be updated to make room for increased growth.
Acorn Analytical Services (UK) Ltd – Making Room To Grow
The Acorn Analytical Services (UK) Ltd business is still growing and knowing that it has a connection and a managed services provider it can rely on, is important. It means the company’s team can focus on meeting the needs of its customers and making sure that growth continues.
The ACS Brochure
We protect your business against ever-evolving threats to your security, both online and offline.
An Agile Working Model
Individuals need to feel trusted and empowered and that demands a radical rethink of working models.
Pushing the boundaries within Law Firms
Traditional law firms are discovering the value in adopting a transformative approach to workplace design.
Tech as a Service
Organisations of all sizes are shifting towards a services-based, pay-as-you-go model for their IT consumption. It’s time to consider technology-as-a-service.
Our New Office Interiors Brochure
We partner with our clients to create productive and inspirational offices.
Workplace Communications Brochure
Our tailored approach simplifies client systems and delivers real business benefits.
ACS Systems acquired by multinational technology company
ACS Systems has been acquired by multinational technology company, Bechtle. Founded in 1983, Bechtle is now one of Europe’s leading IT providers with a presence in 14 countries. In the past, Bechtle direct ...
Evolution of the MSP
Watch Sessions After almost three years, ACS returned to the University of Northampton for their ‘Evolution of the MSP’ event. Guest speakers included Steve Horobin of Arrow, Greg Bayliss of Cymulate and Stephen ...
Bolstering your cyber defences
Since the Russian invasion of the Ukraine, the National Cyber Security Centre (part of GCHQ) has been calling on organisations in the UK to bolster their online defences. For SMEs across the country, however, ...
The Benefits Of VR In Everyday Working Life
The workplace is evolving more than ever, and as proactive participants in the modernisation of workplace design.
Providing the imagination to transform an office
Options abound in the world of office furniture and interiors – and what most businesses need is a designer with an understanding of the market, has original and innovative ideas, and who has an ...
The Evolution of Furniture Solutions
Ask anyone what has been the biggest enabler in our working lives recently and they’ll probably say technology. And they’re probably correct. But hand in hand with that, particularly in light of recent events, is the evolution of furniture solutions to meet the developing needs of a modern office and its workforce.
Microsoft New Commerce Experience & Price Increases – What Does It All Mean?
There are two major aspects to these changes first a global price increase on some of the most popular licensing products for commercial clients.
A Day In The Life – Emily Hudson
A typical day for me is quite varied. I wouldn't say that there is one day that's the same. Which is one of the reasons that I love this job.
A Day In The Life – James Ball
I think what excites me the most is keeping up to date with new technologies and informing people around it because as everything moves along.
Microsoft Defender for Business Bitesize
Microsoft Defender for Business is an endpoint security solution designed especially for the small and medium-sized business (up to 300 employees). With this endpoint security solution, your company’s devices are better protected from ransomware, ...
Upgrade Your Businesses Cyber Security
Why cyber security is important for SMB’S Security is a key challenge for small and medium businesses. In fact, in the past year there has been over a 300% increase1 in ransomware attacks, ...
The Evolution of the MSP – Event Recording
Join ACS Office Solutions, your local strategic IT provider, as we aim to simplify how and why you should choose the right Managed Service Provider (MSP).
What can Virtual Reality do for your organisation?
The emergence of commercial VR technology has contributed to an increased number of innovations, with a wider range of organisations looking for Virtual Reality solutions in 2022.
Introducing Surface Laptop SE for Education
Give students a clamshell device that unlocks learning and new skills with Microsoft 365 for Education, including easy-to-use web experiences.
What should you expect from a strategic IT partner?
Join ACS Office Solutions, your local strategic IT provider, as we aim to clarify how and why you should choose the right Managed Service Provider (MSP).
NCE Webinar Recording
In this video, ACS Director Stephen Harley discusses the upcoming changes to existing and new license agreements that are due to be implemented on 1st March 2022.
Better Education For All: A Webinar Event
Join ACS office solutions and our Microsoft expert for this live webinar as we discover what becomes possible when deploying a 1 to 1 device programme.
Brighter Futures with HP Education
We take the hassle out of IT procurement for you by scoping and supplying the right hardware, configuring devices before delivery.